Connection-oriented vs Connection-less packet switching
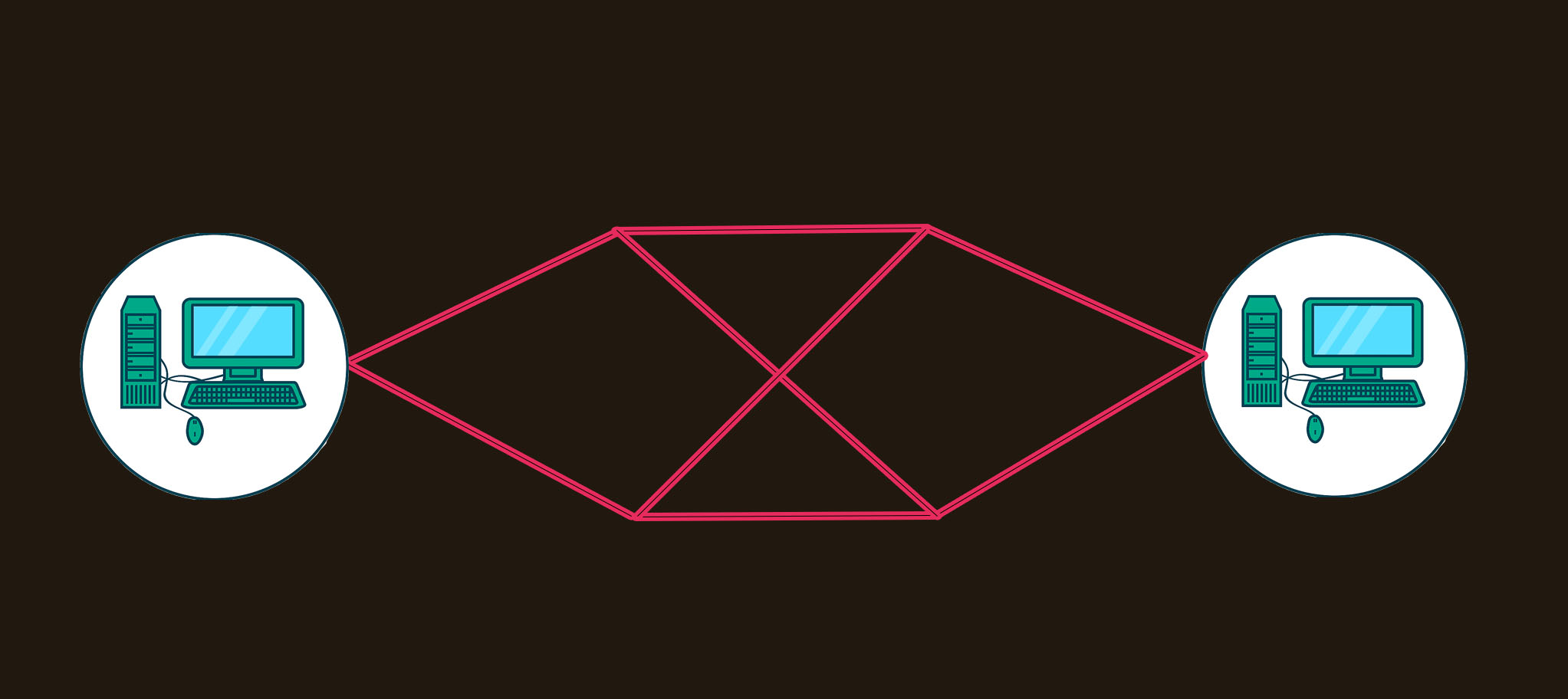
Below shows the comparison of connection-oriented packet switching network and connection-less packet switching , In connection oriented packet switching packets are follow a same route source to the destination while in connectionless packet switching packets don’t follow same route,so in connectionless packets may arrive to the destination in a random manner so it’s required to stored and rearrange the arriving packets. This is a disadvantage of connectionless over connection-oriented packet switching In connectionless packet switching when if there any kind of fault in some choosed transmission link then packets route in a alternative path ,so this is a advantage over connection oriented packet switching(because connection oriented packet switching there is a initial route setup between sender and receiver) Connection oriented is reliable data transfer while connectionless is unreliable. In connectionless there is no initial setup of the connection between sender and the re
